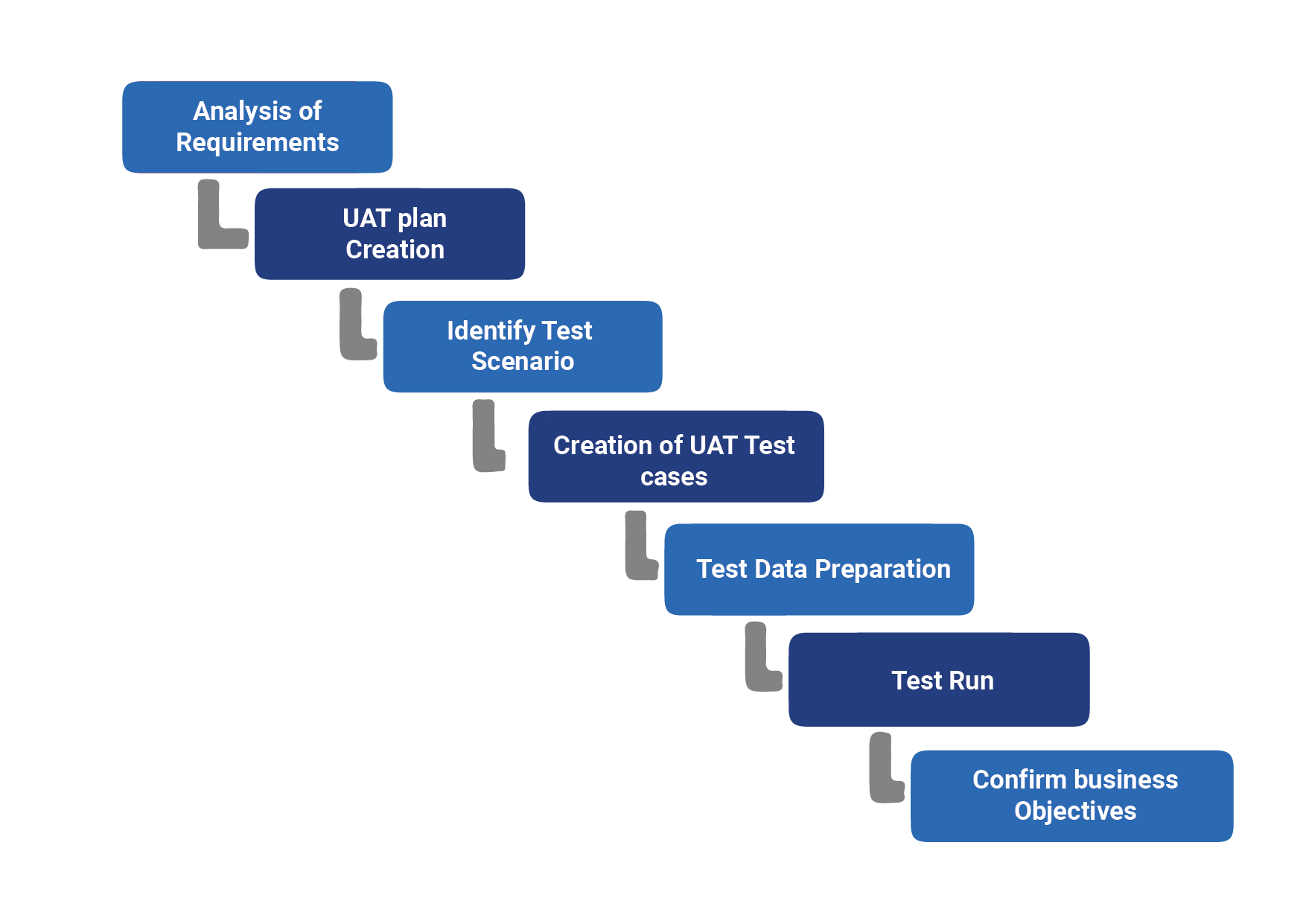
Decades ago, enterprises developed and used heavyweight, script-based automation solutions with traditional software development models. The evolution of scriptless automation tools have changed the ways in which we analyze software and makes the process easier, with a faster turnaround time for users. Scriptless test automation solutions with artificial intelligence approaches help businesses deliver software more efficiently while increasing reusability and reducing manual coding. Excluding the complexities of low-level implementation details, such as learning programming languages and building/maintaining automation frameworks, teams can concentrate on high-level strategic work that adds business value with increased efficiency and collaboration.
Is Scriptless Test Automation the same as Automation Testing
Automation testing is the method of automating user test activities on an application using an automation tool. The automation engineer uses these automation tools to develop test scripts with a programming language. Contrarily, scriptless test automation simplifies the test automation process without actual coding. Scriptless test automation is an effortless and easy way to learn compared with other automation tools. Scriptless test automation aims to solve many challenges that testing teams have been facing. A few of the challenges include:
- Manual test engineers cannot automate test cases
- Test scripts can be reviewed and changed only by people who developed them
- Management and maintenance of test scripts and test data in an agile environment
- The more the scripts, the more time for execution
How Does Scriptless Test Automation Work?
The basic idea of scriptless test automation is that the test creation needs no coding. There are multiple scriptless test automation tools available in the market. The general mechanism is converting front-end representation to machine-understandable code in the back-end to make it work efficiently. For example, IntelliSWAUT uses the test cases written based on UI objects. These simple test objects are compiled and converted into code in the back-end for execution.
IntelliSWAUT — Home-grown Scriptless Testing Tool with AI that Addresses all of your Coding Challenges
IntelliSWAUT is a scriptless automation tool that can automate Web, Windows, API SOAP/REST, Database, and Mobile Applications without writing a single piece of code. The installation process of IntelliSWAUT is simple and can be used by multiple users by accessing the URL to develop and execute tests.
IntelliSWAUT also enables software testers to develop test cases using a user-friendly interface while the actual code is written automatically in the back-end. Using this method, testers can now concentrate on the product’s functionality more efficiently.
Where & How Do I Get Started?
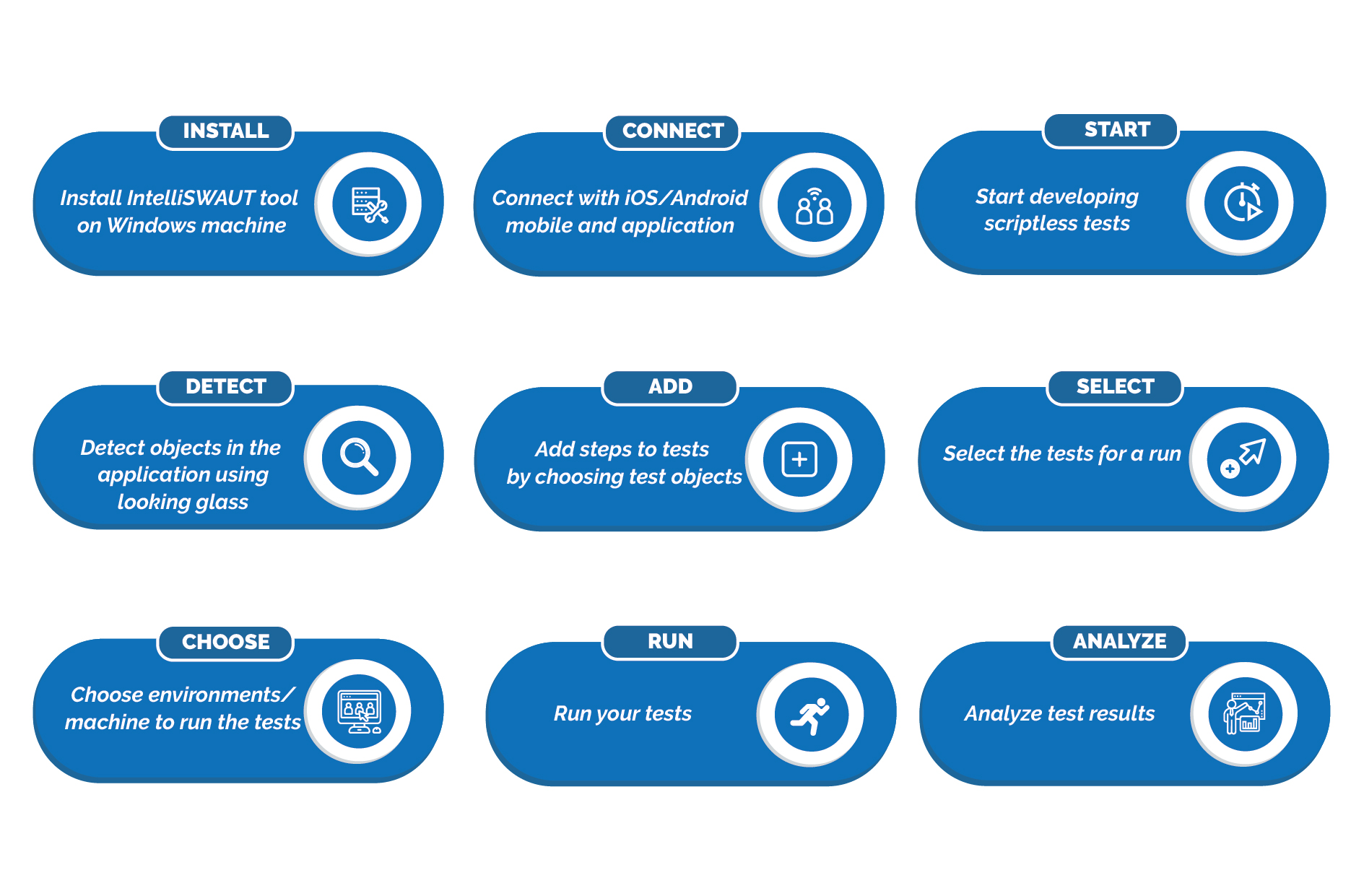
Supported platforms: Windows, Mac
Supported Browsers: IE, Chrome, Firefox
Integration: Jenkins, Jira, Bamboo, Teamcity
Unique features of Sun Technologies’ Codeless Test Automation Solution
- Testers can develop tests without prior coding knowledge
- Applications under automation, which include the frames in UI, are managed automatically by the tool with smart intelligence
- Manual driver updates for browsers are not required since drivers are auto-updated based on the version changes of the browsers
- IntelliSWAUT can automate applications such as Web, Windows, API SOAP/REST, Database, and Mobile Applications
- Test execution results are shared to the stakeholders through email notifications
- Easy integrations with Jenkins for smoke and regression testing
- Testers can execute the scripts on any machine without automation scripts (installation of agents in those machines is required)
- One of the significant advantages is that the projects share the same code base, so upgrading the library is simple (selenium version, reports)
Business benefits of using IntelliSWAUT
IntelliSWAUT is built with the philosophy of bringing development, testing and business-user communities together. In a high power agile environment, this tool helps to bridge the gap among technical and non-technical teams. The incorporated intelligent automation can accelerate performance, maintain speed & quality, and enable real value and ROI.
Using IntelliSWAUT, anyone can automate business process scenarios with 0% coding knowledge, which indirectly saves the cost of hiring skilled developers. By bringing efficiency and agility, the testing standard is easily established among various groups.
The self-healing mechanism of IntelliSWAUT saves 80% of the engineer’s time cutting maintenance, debugging, and fixing change of elements properties in the application on each build.
IntelliSWAUT is a one-stop solution for all of your automation needs. Investment is not required for your diversified automation requirements such as mobile applications, web applications, windows based applications, and API/Web services Automation.
IntelliSWAUT’s smarter reporting capabilities deliver the executions results in reports to the stakeholders automatically, through emails and SMS notifications.
Conclusion
Every QA organization should focus on test automation areas by finding the greatest constraint/ challenges in their software development life cycle (SDLC). The risk of not investing in a particular test automation solution can lead to a loss in your competitive advantage and reduced agility and innovation.
With scriptless test automation versatility and ease of use, it is the perfect fit for projects with tight deadlines and a dynamic scope. The process makes automation simple and helps stakeholders to concentrate on a high business context.
Our testing experience has seen an overall increase in software quality by identifying defects early and improving accuracy in future defect classifications. Swift test automation techniques identify and isolate hard-to-detect quality issues such as overall user experience, quality of service (QoS), availability, scalability, and performance. IntelliSWAUT provides decision support by automatically correlating test metrics to corresponding business metrics.

Vaidyanathan Ganesa Sankaran
Vaidy is an experienced lead Solutions Architect heading sales and project delivery for Cloud (AWS, Azure), DevOps and legacy Modernization projects with a demonstrated history of working in the information technology and services industry. He is a strong engineering professional with a Master of Science (MS) focused in Computer Software Engineering from BITS Pilani. He has the capability to manage bigger teams and generate revenue through new Sales and Account Mining.
Recent Posts
Have you ever tried IntelliSWAUT?
IntelliSWAUT is one of the best scriptless testing tools, and it is becoming popular in the market.

Sugumar Shanmugam
Sugumar Shanmugam an Automation Evangelist with 13 years of experience with Test Automation and has pioneered various test automation tools. He has authored many whitepapers and blogs for various summits. His key specialties and capabilities with specialized platforms are Mobile Automation and Performance, Data Science, AI & ML, and DevOps.